Whether you’re sending email as an individual or for business, hackers don’t discriminate when hacking your email client! So, let’s explore how you can protect your emails with seven practical tips
If you frequently send confidential personal or professional data by email, you probably want to know how to secure an email.
A vigilant email user can often weed out incoming fake or phishing emails. But what can you do to secure your outgoing email communications? If someone intercepts your outgoing messages, they can read all the content and use it however they like. And what happens if someone hacks your email client itself? Then, they can not only read all your emails but also impersonate you and send emails to your entire contact list!
In this article, you’ll find seven tricks on how to protect your email. If you’re looking for tips on how to recognize fake or phishing emails, please refer to this article: How to Tell If an Email Is Fake.
1. Enable E2E Encryption
You might not be aware that when you use generic email clients like Gmail, Yahoo, Hotmail and the like, the email first passes through these service providers’ servers and other endpoints before being redirected to the recipient’s server.
Although these services use standard TLS technology, which protects emails while they’re in transit by encrypting the transmission channel, TLS doesn’t encrypt the message itself. The transmission of email between multiple endpoints increases the chances that your message will be compromised.
A stronger encryption layer for emails is end-to-end (E2E) encryption. E2E encrypts the email message and attachments before they leave your inbox, meaning that they’re secure:
- While they are in transit (traveling from your outbound mail server to the recipient’s inbound mail server), and
- When they’re at rest (i.e., stored in your recipient’s inbox on their mail server).
Some email service providers provide end-to-end encryption for free. The most well-known E2E service providers are ProtonMail, Mailfence, and Tutanota. Basic accounts are free with limited storage, and if you want an email address with your company domain name or more storage space, you can upgrade to a premium plan. However, both you and your recipients must use the same email provider to send encrypted messages.
Alternative Option: Use an S/MIME Certificate
So, how can you communicate securely with users of other email platforms? You can also use S/MIME certificates, or what are otherwise known as email signing certificates. These digital certificates not only help you provide E2E encryption, but they also allow you to attach your digital signatures to all outgoing emails. Digital signatures are a form of verifiable identity that can’t be modified, deleted, or copied. Adding a digital signature to your outbound messages helps you to provide a strong defense against phishing and spoofing attacks.
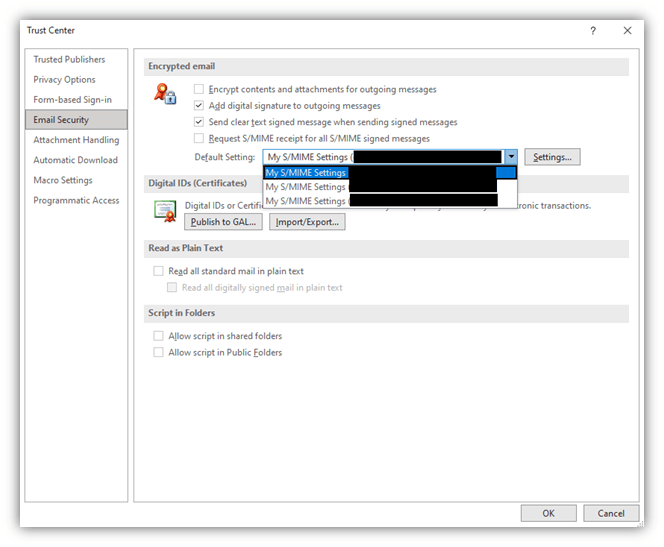
An example of email signing certificates in Outlook.
Here’s where you can find a great step-by-step resource on how to install an S/MIME certificate in Outlook as well.
2. Install Security Extensions and Add-ons
The E2E enabled email clients mentioned above can be complicated to use. If you want E2E functionality with your regular email clients, there are several browser extensions and add-ons you can use to secure your emails. By installing these tools, you can enable E2E encryption, set expiration, disable forwarding, revoke access to email, and watermark attachments with recipients’ names to prevent them from leaking sensitive files.
Here are some well-known extensions:
3. Enable Two-Factor Authentication or 2-Step Verification on Your Account
Our third topic on how to secure an email in terms of account protection relates to two-factor authentication, or what’s known as 2FA. With two-factor authentication for email, you will get a unique one-time password or PIN (OTP), URL, or code on your registered mobile device or via a secondary email address. You need to provide this along with the password every time you log in.
It may sound like a hassle, but using 2FA to protect your email account is definitely a good practice.
Check out these resources to get more information on how to enable 2FA on these email specific clients:
- Apple Mail,
- Gmail,
- Yahoo Mail,
- Microsoft, and
- AOL.
You can also enable 2FA for account security using these apps:
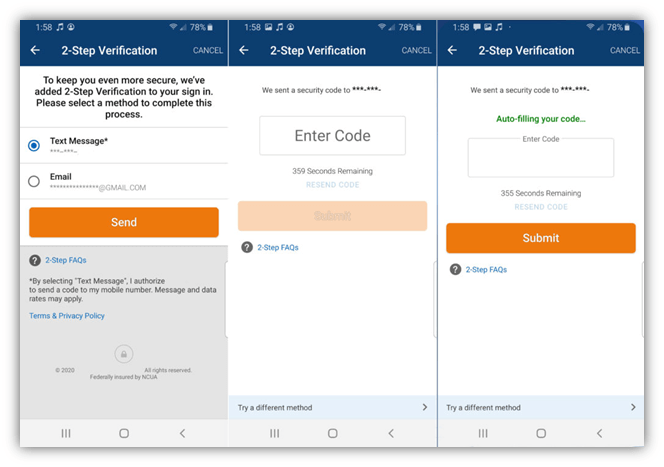
A series of screenshots showing two-step verification, where the OTP is sent via SMS text message.
4. Encrypt Attachments Using Other Methods
But what do you do if you don’t have an email signing certificate but still want to encrypt your email attachments? If you’re sending important data as email attachments, it’s always a good practice to encrypt those files. In general, when you password-protect a document, it gets encrypted. For any Microsoft products (Word, Excel, PowerPoint, Access), you can go to:
Files > Info > Protect Document/Workbook > Encrypt with Password
There are also free encryption software programs available that you can use — a few examples of which include Folder Lock, 7-Zip, VeraCrypt, AxCrypt, and DiskCryptor.
Please make sure you send the recipient’s password in a separate email, via SMS, or by some other channel.
5. Don’t Let Browsers Save Your Passwords
Using the auto-login capability is certainly convenient, but it’s not good for protecting your email. When you store passwords in your device’s browser, anyone with access to your device can read them. To see how many passwords you have saved or to make changes to those settings in Chrome, do the following:
- Go to the menu (three vertical dots on the upper right side).
- Click on
- Locate Autofill and click on Passwords.
Here, you can see how many passwords you have stored. You can also view individual passwords by clicking on the eye symbol next to them and even export the passwords in an Excel sheet. If you lose your device or a hacker takes control of it using malware, they can easily intercept these passwords. It’s best to delete these stored passwords and type your passwords manually when logging in.
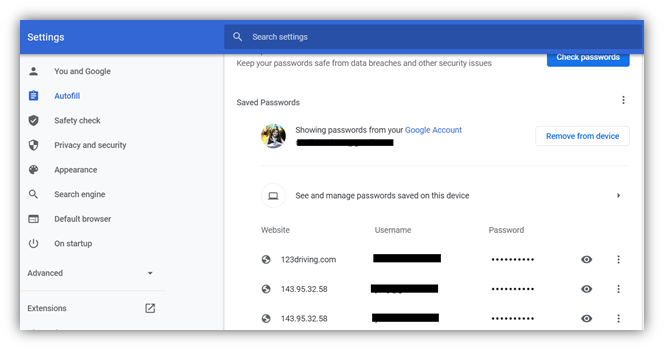
A screenshot from Chrome showing examples of stored passwords in the Autofill settings.
6. Have Separate Email Accounts for Essential and Non-Essential Use
According to Dashlane, the average American internet user will have 300 online accounts by the year 2022. Whenever you try to sign up for a new service or account with a website, you typically have to provide the site with an email address. This email address will be associated with your account from this point on (until you decide to change it in the future). That means your email ID is exposed to a lot of different platforms.
In many cases, this is fine. But if their database data leaks or if these platforms sell this data to others (that’s illegal, but it happens), you’ll not only get tons of phishing and spam emails but your email account may face brute force and credential stuffing attacks. This is why it’s a good idea to keep multiple email accounts.
It is highly advisable to keep one account for important tasks like banking, utilities, insurance, and personal emails. You can also have a different email account for any non-essential services (such as email sign-ups, coupons, etc.). And remember, never reuse passwords across multiple accounts or share your password with other users. It’s a best practice to use a unique, strong password (or, ideally, passphrase) for each account that only you know.
7. Don’t Log In to Services Using Your Email Accounts (or Other Unrelated Accounts)
We know it’s convenient when a new platform gives you options like “Login with Gmail” or “Login with Facebook.” After all, you don’t need to fill out their boring form and you’re done in a click! However, it is a highly unsafe practice. Do you always read the full terms and conditions when signing up for accounts or services? The organization might be able to see all the personal information you have saved on your Gmail or Facebook, and use that data.
Some platforms’ policies are so intrusive that they get access to your contact list, emails, media files, and social media posts as well. They can invade your privacy and use this data for marketing purposes. And imagine what can happen if the platform’s database or server is hacked — the hacker can cause huge damage with this access such as by:
- Sending phishing emails using your email client,
- Blackmailing you, or
- Using their access to perform any number of other harassing or illegal actions.
Steps to Prevent Rainbow Table Attacks
Salting your passwords prior to hashing them is the chief way to prevent rainbow table attacks. Don’t use the same salt for all passwords — use a unique, unpredictable salt for each one. A salt is an unpredictable element and prevents an attacker from creating an effective rainbow table in advance. According to McAfee, you’ll want the salt value to be the same as the hash output.
Final Words on How to Secure Your Email
There are approximately 4.147 billion email users in the world as of 2021, according to data from Radicati. Such a large pool of potential victims is a huge attraction for cybercriminals. That’s why it’s critical that you know how to protect your emails. This includes how to recognize phishing incoming emails and how to secure outgoing emails. For the latter, you can do the following to secure an email account:
- Use encryption for attachments
- Enable 2FA and E2E encryption,
- Install security tools and extensions,
- Delete passwords from browsers,
- Keep separate email accounts for essential and non-essential work, and
- Don’t log in to other services using default email clients.
Stop Hackers From Hacking Your Business!
Get DigiCert Secure Site Pro OV SSL that includes a vulnerability scanner, malware detector, PCI scanners, website backup, multi-domain security, and many more advanced security tools.Shop Now