BuiltWith data shows that more than 66% of the top one million sites use the SSL communication protocol (or, more accurately, the TLS communication protocol) by default. Here’s a beginner’s guide on how SSL communication works and how it protects the data that transfers between a customer’s client and your server
If you are a website owner concerned about security, you’re not alone! Two in three (68%) business leaders recognize that cybersecurity threats to their businesses are increasing. In a survey by CyberEdge, 86% of organizations reported they were victims of a successful cyber attack in 2020.
Such statistics show that you must equip your website with robust security tools and the latest technologies. One such essential security product is an SSL/TLS certificate to facilitate secure SSL communication. But how exactly is SSL communication and how does SSL technology work? Let’s explore that process more in layman’s terms.
What Is SSL Communication?
The secure socket layer (SSL) protocol is designed to secure communication between two endpoints using public key infrastructure (PKI) technology. These endpoints could be a website, browser, application, email client, etc. The SSL certificate enables SSL communication. It verifies the identity of the server and facilitates the data transfer through a secure, encrypted tunnel.
Please note that SSL communication and TLS communication are the same things in a general sense — SSL and TLS are both protocols that secure data in transit to ensure that only the two intended parties have access to it. However, it’s important to note that they’re different technically in terms of how each process works. But since it’s common within the industry to refer to SSL and TLS in the same way, we’ll use both terms interchangeably throughout the article.
There are two main parts of SSL communication:
1. Encryption
When you use the internet to transfer data from one endpoint to another, it uses an insecure protocol called HTTP (hypertext transfer protocol) that exchanges data via port 80. It’s easy for hackers to intercept communications conducted via HTTP because the data is transmitted in plaintext format. To enable the use of a secure protocol, website owners must install something known as an SSL certificate (or, more accurately, a TLS certificate) on their website’s server.
An SSL/TLS certificate creates a secured encrypted tunnel for data transfer, which is known as HTTPS (hypertext transfer protocol secure). It’s like a protective shield around the HTTP channel. Hackers can’t intercept the data while it is in transit through HTTPS, as it uses port 443, which is secure.
A graphical illustration of how encryption works
2. Identity Verification
Before issuing an SSL certificate to a website, a third-party certificate authority (CA) verifies the applicant website’s identity to make sure users are connected to the right website. All the sites have their unique public key and their corresponding private key. The CA’s responsibility is to attach the right public key to the right website (hostname) in the SSL certificate. They do this by verifying company records and information during a validation process.
There are three levels of validation for SSL/TLS certificates:
Domain Validation (DV)
Domain validation is the most basic level of validation and only verifies that the certificate requestor is in control of the domain. This makes a secure padlock icon appear in your browser, but it doesn’t validate the identity of the organization or individual that controls the domain.
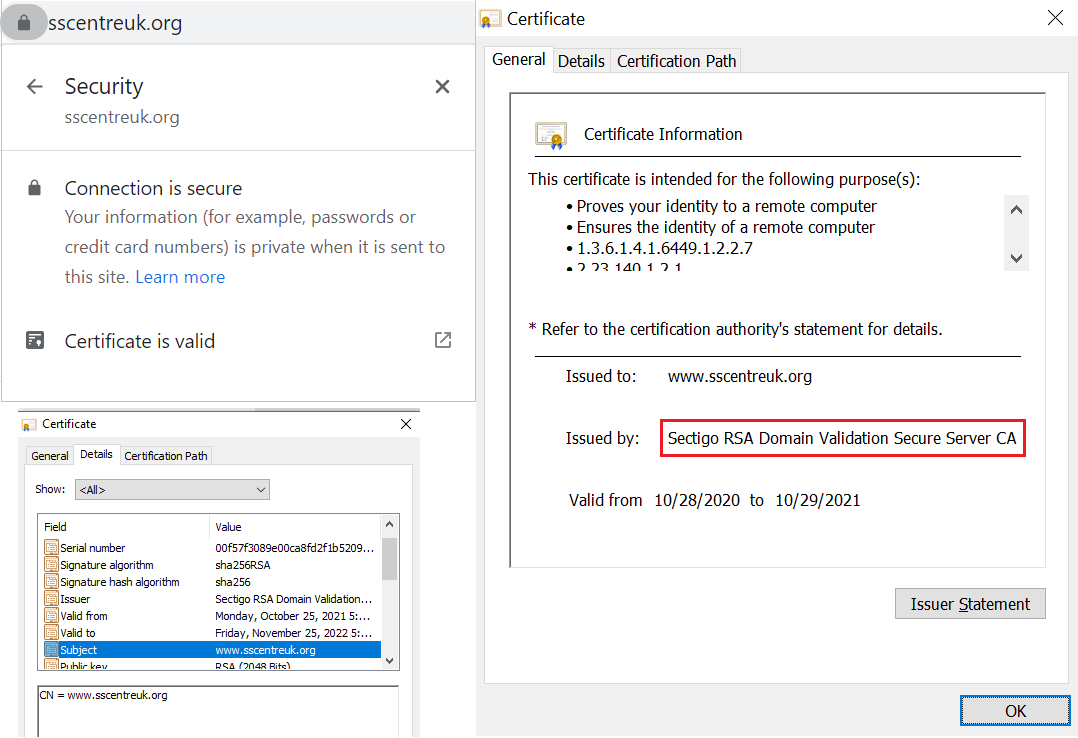
Organization Validation (OV)
Organization validation is what’s known as basic business validation because it requires basic verification of the organization’s digital identity in addition to its ownership of the domain.
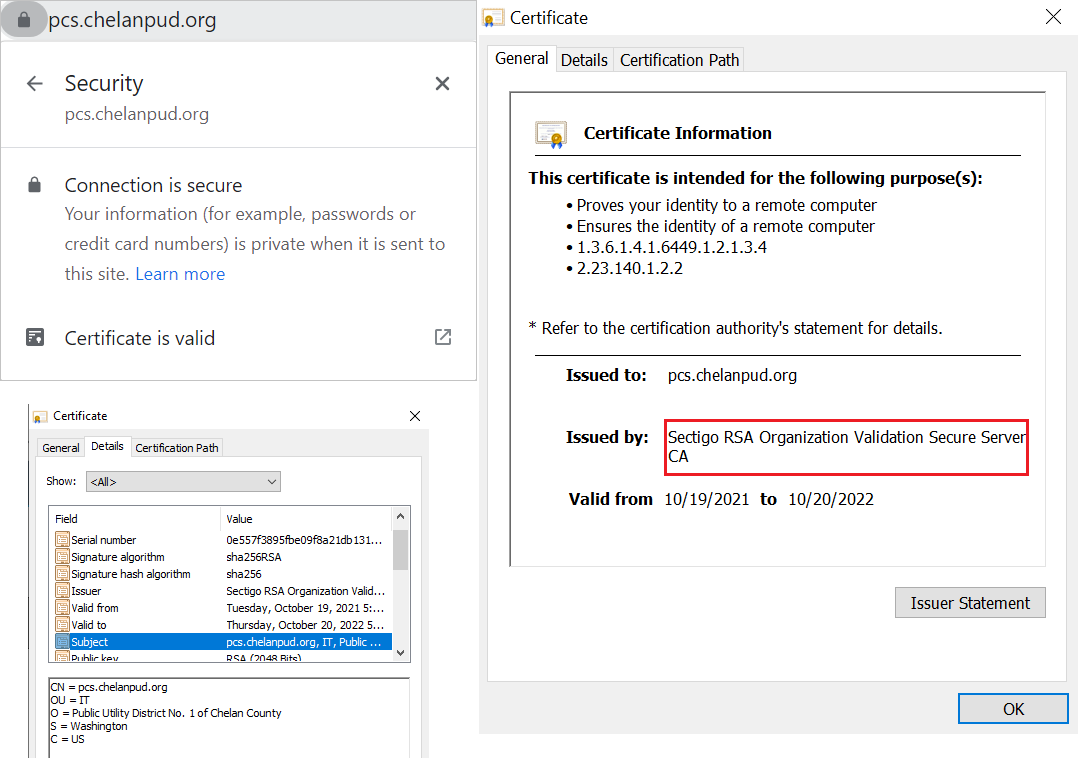
Extended Validation (EV)
Extended validation is the highest level of validation and requires the most rigorous verification process (domain + extended business validation). This enables verified company information to display in users’ browsers when they visit your website:
Once the validation process is complete, the CA signs the SSL/TLS certificate from its own private key. This assures browsers and users that the public key stated in the certificate (and its private key) truly belongs to the hostname mentioned in the certificate. That’s how the CA ensures that the encrypted traffic reaches the correct website’s server.
We have just written the identity verification in an easy version, but it’s a long and technical procedure with various levels of identity verification involved. To understand it in detail, these are the sources you can use: SSL Verification Process and Role of the Certificate Authority
The Role of Identity & Encryption in Online SSL Communications
To help you imagine this, let’s say you’ve ordered a shirt from Amazon for your significant other as a gift. The delivery person carries the garment in a transparent plastic bag to your place. While the shirt is in transit from the seller to your home, anyone along the way can see what kind of shirt you have ordered. This isn’t good for privacy and hampers your ability to surprise your loved one. And if they don’t take steps to verify your identity (so that they know they’re delivering the package to the right person), then it means that virtually anyone can wind up receiving that package.
An SSL certificate is like one of the cardboard boxes that Amazon employees pack products in. Once the product is inside the brown packaging, no one can see what’s inside while it is in transit until it arrives at your home and you open it. Secondly, the delivery person takes your signature to ensure they have delivered the package to the right person so only the authorized person opens it.
Similarly, the data in transit between a website and its users stays protected when it is guarded by the SSL communication protocol and it reaches the right server.
Why Does SSL/TLS Communication Matter?
You might be asking questions like, “Do I really need an SSL certificate for my website?” and “Is SSL communication really worth it?” — here are your answers. Let’s quickly explore five reasons why an SSL certificate is crucial to your organization or business:
- Asserts your organization’s digital identity. When you use SSL/TLS certificates with specific validation levels (OV and EV), you’re providing users with a way to verify that your website is legitimate.
- Enables you to protect your users’ data. SSL/TLS helps to protect users’ data against man-in-the-middle (MitM) attacks, eavesdropping, data leaks, ISP snooping, and other privacy threats.
- Helps you boost your site’s Google rankings. The HTTPS protocol is one of the key SEO elements. If all the factors are the same, the website with an SSL certificate will be ranked higher than the one without it. Basically, HTTPS is mandatory. Google made using the secure SSL/TLS protocol mandatory for websites since the release of Chrome 68 in 2018. (Other major browsers have implemented the same requirement.)
- Improves browsers trust your website is legitimate. An SSL certificate replaces the “Not secure” warning with a padlock icon in the address bar. A padlock sign shows customers that they have connected to the right website and their data will be securely transferred to the server.
- It’s needed for legal compliance. Encryption is part of most of the security and privacy laws. As an SSL certificate provides encryption between two endpoints, it is needed to be compliant with the major regulations. Here is a detailed article: Encryption requirement by 10 major laws.
How Does SSL Communication Between a Client and Server Take Place?
An SSL certificate uses PKI technology to encrypt the communication channel, although it doesn’t encrypt the message itself. A TLS certificate facilitates two types of encryption methods: asymmetric and symmetric. Before moving forward, let’s understand the basic concepts of symmetric and asymmetric encryption and how they work.
Symmetric Encryption
Here, the same key is used for encryption and decryption. An SSL certificate facilitates using a symmetric key called a “session key.” The encrypted text is called ciphertext.
A graphic illustration of how symmetric encryption works
Asymmetric Encryption
Here, two separate types of keys are used; a public key for encryption (locking the data) and a private key for decryption (unlocking the data). The public key is stored in the website’s SSL certificate and is accessible to all. The corresponding private key stays secured within the website’s server. SSL technology uses asymmetric encryption to encrypt and decrypt the session key.
A graphic illustration of how asymmetric encryption works
Breaking Down How SSL/TLS Communication Works
Now, let’s consider a real-life example of how SSL communication between client and server works.
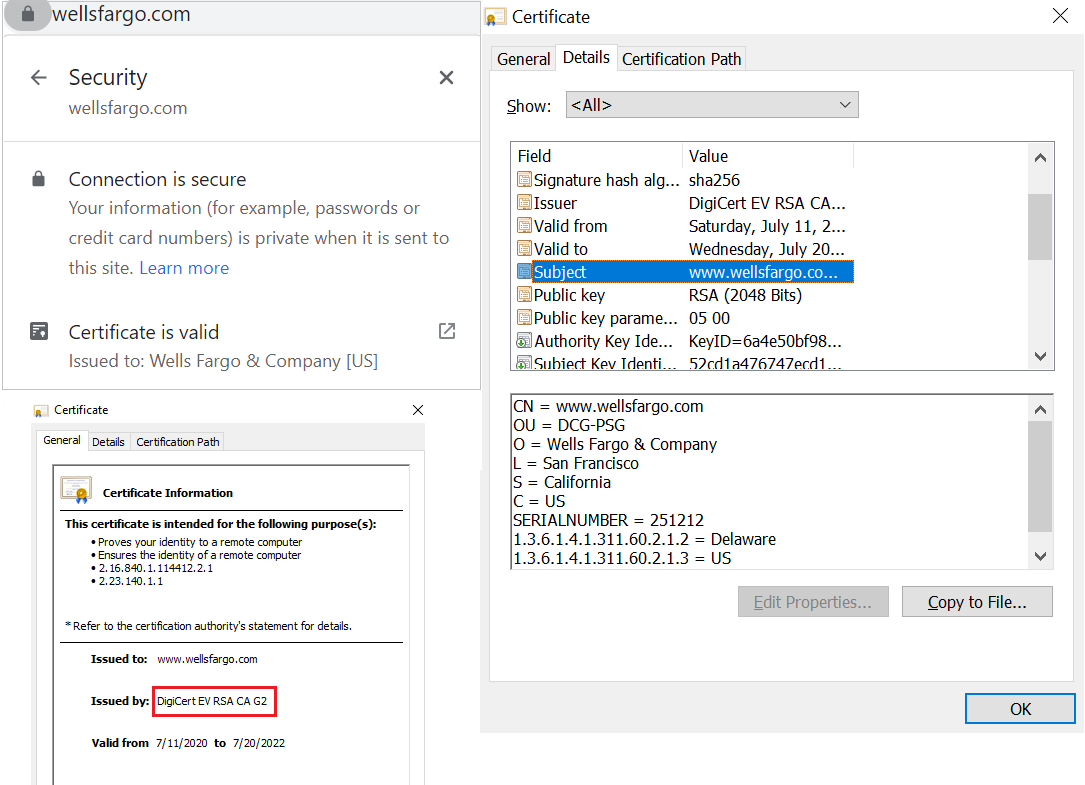
Let’s say you want to check your bank balance online. You open Google Chrome and type “wellsfargo.com” in the address bar. What occurs between your browser and the website’s server can be broken down into four overarching steps. Here’s how the SSL communication process works from that point:
Step 1: The Server and Client Exchange “Hello” Messages
Your browser sends a ClientHello message to wellsfargo.com’s server. The message contains the cipher suites and the TLS version it requires to make an HTTPS connection. Wells Fargo’s server responds with a ServerHello message informing the browser whether it is able to support the algorithms and TLS version demanded by the browser. This process is known as a TLS handshake.
Step 2: Verifying the SSL/TLS Certificate and CA Signature
Along with the ServerHello message, the server sends its SSL certificate as a text file containing wellsfargo.com’s public key, hostname (domain name), issuance and expiry dates, and information about the issuer of the certificate. Chrome checks all these pieces of information and verifies the certificate authority’s (CA) signature.
If everything checks out, it moves forward to the next step. If not, the browser will show an error message like “Your connection is not private” or “Potential security risk ahead.”
Step 3: Session Key Generation
Now, Chrome creates a random session key, encrypts it using wellsfargo.com’s public keys stored in its SSL/TLS certificate, and sends it to the server. To decrypt the session key, Wells Fargo’s server uses a unique private key, which is mathematically related to the public key. At this point, asymmetric encryption is used, where the public key from the SSL certificate and the private key from the server is utilized.
Step-4: Establishing TLS Communication Via HTTPS Channel
Now, all the data will travel between your browser and wellsfargo.com’s server using a secure HTTPS channel. Both parties will use this asymmetrically encrypted connection to exchange data that allows them to create identical copies of a symmetric session key. They will use this session key to encrypt and decrypt data for the rest of the session.
But why would they switch to using symmetric encryption? Symmetric encryption session keys are less bulky and burdensome cryptographic operations. By switching to symmetric encryption, the SSL communication is faster.
Of course, to access, decrypt and read the communications between you and the bank, a hacker needs access to that session key (which they won’t have). This means that even if the attacker accesses the encrypted data while it’s in transit, all they’ll get is a bunch of incomprehensible text which they won’t be able to interpret. So, SSL communication means communication conducted via an HTTPS channel, which is robustly secured by asymmetric and symmetric encryption.
You must have noted here that the communications start out using asymmetric encryption to securely exchange information in order to establish symmetric encryption. Basically, asymmetric encryption is a resource-intensive slow process compared to symmetric encryption (at scale), so it’s only used as a means to help the two parties negotiate a secure symmetric encryption connection. Because they’re then using the same key, it’s faster and less resource-intensive at scale.
TL;DR: A Summary of What SSL Communication Is & How It Works
Okay, we get it. You’re short on time and just want to glean the highlights of this article. These are the main takeaway points for the SSL communication topic:
- SSL communication means that data transferred between two endpoints is done via the HTTPS 443 port. An SSL/TLS certificate is required to facilitate the TLS communication.
- Certificate authorities carry out one of three levels of validation (DV, OV or EV) to verify domain ownership and/or organization information about the certificate requestor.
- The two parties (your customer’s browser and your website’s server) use asymmetric encryption to exchange information. This allows them to generate a session key.
- The communication between a server and browser is enveloped in a session key, which is encrypted using a website’s public key and decrypted using its corresponding private key. This symmetrically encrypted connection enables the two parties to communicate data via a secure channel.
- As long as the private key is securely stored with a website’s servers, no one can use it to generate the session key and decrypt the encrypted data in transit.
- The HTTPS channel helps to prevent data theft, eavesdropping, and MitM attacks.